What Does a Compliance Officer Do? Your 2024 Career Guide
What Does a Data Analyst Do? Your 2024 Career Guide September 19, 2024 Compliance | Risk Management Table of Contents A compliance officer is a crucial role within organizations, ensuring that they adhere to various laws, regulations, and industry standards. They act as the organization’s conscience, safeguarding its reputation and…
Top 7 Important Activities for Banks to Manage their Compliance Effectively in 2024
Top 7 Important Activities for Banks to Manage their Compliance Effectively in 2024 August 23, 2024 Compliance | Risk Management Table of Contents In today’s complex financial landscape, banks face a myriad of regulatory challenges. From data privacy to anti-money laundering, ensuring compliance is crucial to maintaining a strong reputation,…
Top 10 Risk Management Software in 2024
Top 10 Risk Management Software in 2024 July 5, 2024 Compliance | Risk Management In today’s complex business landscape, effective risk management is crucial for organizational success. The right software can significantly streamline this process, providing valuable insights, automating tasks, and ensuring compliance. Here’s a look at some of the…
The Ultimate Guide to Compliance Risk Management
The Ultimate Guide to Compliance Risk Management June 18, 2024 Compliance | Risk Management Table of Contents Ever feel like your business is navigating a minefield of regulations? That’s where compliance risk management comes in. This guide will equip you to understand and navigate this crucial aspect of business success. What…
6 Steps to Prevent Data Breaches in 2024
6 Steps to Prevent Data Breaches in 2019 May 8, 2019 Corporate Security | Cyber Security | RiskWatch Blog | Third Party Risks How to Protect Against Data Breaches in 2024 The list of companies suffering data breaches is surprising, especially when many are sizeable companies with plenty of data…
Top 5 Risks in Construction
Top 5 Risks in Construction July 14, 2020 Construction | Risk Assessment & Compliance | RiskWatch Blog Construction Risk According to the U.S. Census Bureau, the U.S. construction industry was worth $1.3 trillion in 2019. Within such a large industry like construction, risk is inherent in all activities. Depending on…
How Often Should Healthcare Organizations Assess Their Compliance Programs?
How Often Should Healthcare Organizations Assess Their Compliance Programs? May 21, 2024 Compliance | Regulatory Compliance | Risk Assessment | RiskWatch Blog | Utilities Healthcare organizations operate in a complex and highly regulated environment. Compliance programs are essential to ensure that these organizations adhere to all relevant laws, regulations, and…
Top 4 Compliance Challenges in the Energy and Utilities Sector in 2024
Top 4 Compliance Challenges in the Energy and Utilities Sector in 2024 April 11, 2024 Compliance | Regulatory Compliance | Risk Assessment | RiskWatch Blog | Utilities The utilities sector faces a multitude of compliance challenges due to its critical role in providing essential services such as electricity, gas, and…
Ultimate Guide to Compliance & Risk Management for Utilities Companies
Ultimate Guide to Compliance & Risk Management for Utilities Companies April 8, 2024 Compliance | Regulatory Compliance | Risk Assessment | RiskWatch Blog | Utilities Introduction In the ever-evolving landscape of the utilities sector, Compliance & Risk Management has become a critical component of operations. As regulatory requirements continue to…
What Type of Businesses Need to Comply with PCI DSS?
What Type of Businesses Need to Comply with PCI DSS? March 21, 2024 Compliance | Design | Managing the Risk Assessment | Regulatory Compliance | Risk Assessment | RiskWatch Blog The Payment Card Industry Data Security Standard (PCI DSS) is a set of security controls designed to ensure that all…
How to Use Automated Assessment Software to Manage and Meet Your Security and Compliance Requirements
How to Use Automated Assessment Software to Manage and Meet Your Security and Compliance Requirements Security and compliance are two essential aspects of any organization, especially in today’s complex and dynamic environment. However, managing and meeting these requirements can be challenging, time-consuming, and costly, especially if done manually or with…
Oil and Gas Risk Management
Oil and Gas Risk Management November 21, 2019 Oil & Gas | Risk Assessment & Compliance | Riskwatch Blog Oil and Gas Industry The oil and gas industry is a volatile one, inundated by a number of risks and regulations which range from worker safety to environmental concern. It is…
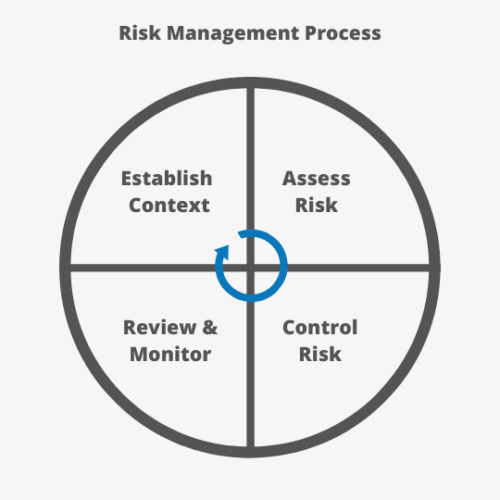
Risk Management Process: Security Analysis Methodology in SecureWatch
Risk Management Process: Security Analysis Methodology in SecureWatch March 19, 2018 Managing the Risk Assessment | Risk Assessment | Risk Assessment & Compliance | Threat Assessment What is ISO 31000? ISO 31000 is a security analysis methodology, or risk management process, that is used in various risk programs across a…
What is a Gap Analysis?
What is a Gap Analysis? November 18, 2019 Gap Analysis | Riskwatch Blog Gap Analysis A gap analysis is a necessary component of risk management that is, at times, unclear to those in risk, security, and compliance positions. This leaves the question of, “What is a gap analysis?” Simply put,…
Top 5 Risks in Education
Top 5 Risks in Education January 15, 2020 Compliance | Education | Physical Security | RiskWatch Blog Risks in Education Whether students are 6-years-old or 40, educational institutions are responsible for providing them with a safe, productive learning environment free of risks. Education risk management is becoming increasingly important as…
The Importance of Risk Monitoring
The Importance of Risk Monitoring August 13, 2021 Design | Managing the Risk Assessment | Risk Assessment | Riskwatch Blog Risk Monitoring Overview Risk monitoring is a crucial step in the total risk management process. Unfortunately, there is never a true end to the risk management process; risk monitoring will…
The CAN-SPAM Act
The CAN-SPAM Act February 13, 2020 Compliance | Regulatory Compliance | Riskwatch Blog What Is the CAN-SPAM Act? The CAN-SPAM Act essentially dictates what can and cannot be done in regards to commercial messaging, including what can happen if you’re noncompliant. Formally referred to as The Controlling the Assault of…
Risk Management in Banking
Risk Management in Banking December 9, 2020 Financial Services | Risk Management | Riskwatch Blog Risk management in banking has largely been focused on compliance with regulations and standards in recent times. This practice primarily stems from the regulations and culture that emerged during the global financial crisis that took…
Top Three Industries that Need an Effective Risk Management Solution
Top Three Industries that Need an Effective Risk Management Solution February 9, 2024 Compliance | Cyber Security | Cyber Threats | Disaster Recovery Planning | Emergency Preparedness | HIPAA Risk Analysis | Hospital Security | Managing the Risk Assessment | OSHA | Regulatory Compliance | Risk Assessment | Risk Assessment…
Top Five Supplier Risk
Top Five Supplier Risk July 5, 2018 Compliance | Emergency Preparedness | Managing the Risk Assessment | Risk Assessment | Risk Assessment & Compliance | Third Party Risks | Uncategorized A supplier can be defined as a person or organization that provides a product or service to a vendor. Most…
Welcome to our Blog
We post on different topics, mostly related to risk and compliance. Let us know if there’s anything in particular you want us to cover and if we can’t make a blog out of it, we’ll try to send you some information. Be sure to subscribe so you don’t miss out!
Subscribe for our latest posts
Join us to get the latest news from Riskwatch.