Vendor Risks
The Challenges
Without a risk-based approach to managing vendors, your organization is vulnerable to all of the risks that are associated with your vendor. It is difficult enough to manage risks for your own organization, so how can your team manage risks for another organization as well?
Vendor risks include cybersecurity, compliance, physical security, reputational, financial, operational, strategic, and more. A process that includes all of these areas is challenging to create, costing a lot of resources and there is still no automation, meaning the process takes up employee time and leaves room for inaccuracies.
Pain points include selecting quality and relevant frameworks, collecting data, analyzing data, setting remedial tasks, following up on progress, creating reports, and more.
The Impact
A vulnerability for a vendor is a vulnerability for any organization that has partnered with them as well because the vendor plays a crucial role in the organization’s business processes, as well as access to organizational secrets and private data.
If a vendor experiences a data breach, all of their partners are at risk of having stolen data and it’s the partners who are responsible for that data. This affects the company and their customers, resulting in severe financial losses due to fines, compensation, loss of business from downtime and reputational damage, potential ransomware, and more.
Companies are responsible for performing due diligence on vendors and are responsible for data that customers give to them, making it difficult to prove that you weren’t negligent unless you have a thorough risk management platform that stores reports with all efforts.
Achieve your Vendor Risk Management Goals with RiskWatch
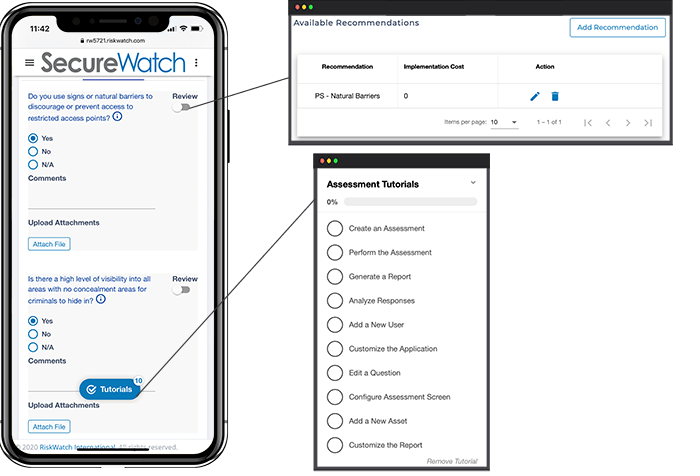
Prebuilt Content Libraries
RiskWatch offers over 50 prebuilt content libraries that are ready for use in our platform. These libraries contain industry standards and regulations, lending subject matter expertise and guidance for organizations. Achieving compliance with these libraries ensures risk is minimized.
- Additional content libraries can be added to assessments with a single click.
- Reduce unnecessary costs by eliminating the need for third-party expertise.
- Custom libraries and any standard or regulation not already available can be created.
Automated Analysis
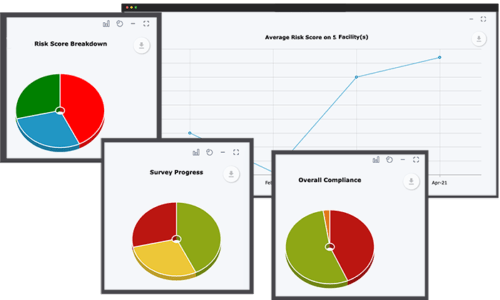
RiskWatch software streamlines the assessment process, using our intelligent analysis methodology to collect all relevant security data and highlighting any security gaps. Automated analysis aims to improve security positioning without the need to manually compare site data and risk scoring prioritizes projects, allowing you to manage security without getting stuck in the weeds.
- Automatically rank sites by risk to prioritize mitigation.
- Understand security at a glance with real-time dashboard analytics.
- 80% time savings when assessments were conducted using previous assessments performed in SecureWatch and compared to a manual assessment process.
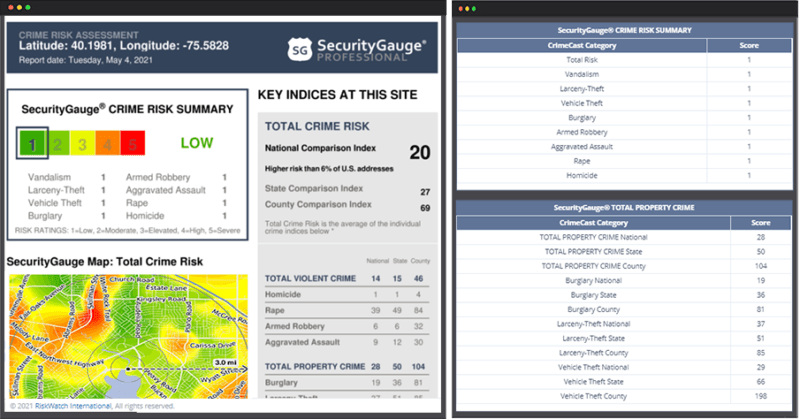
Third-Party Data
RiskWatch partners with third-party data companies to give accurate risk scoring per facility, based not only on your security assessment but also on crime data for the surrounding area as well. Data registers and third-party data providers can be used to populate new assessments with standard sets of data and determine the likelihood of an incident objectively.
- Partners include Cap Index, Security Gauge, and World Aware.
- Increase visibility and transparency with facilities, enabling more insightful decisions.
- Communicate the status of facility security to business stakeholders using a unique security risk rating for each facility.