RiskWatch Implementation
Where to Start?
Step 1
Start for Free
Our software is free to use – no payment information is required. Once you’ve met your limit of free assessments, extend your use by purchasing licenses based on the number of Users or the number of Areas you will be assessing.
Step 2
Purchase Licenses
How Many Users? Our Pricing is based on how many user accounts you will have or how many areas you will be assessing. Each User or Area to be assessed requires 1 license. An Area is anything that is the target of an assessment, such as a facility, supplier, client, etc. We provide quantity discounts on licenses.
Step 3
Select Content
Select your content libraries. This will be relevant to the type of assessment you’re performing, such as using our HIPAA library in a hospital security assessment or our ASIS library in a vendor physical security assessment. You can also upload any of your own content.
Step 4
Configure and Assess
Create specific users and assets. Once user accounts and assets are created, you can create/begin assessments. Do a preliminary assessment to see where risk lies and then create a custom report to see the data gathered from the assessment.
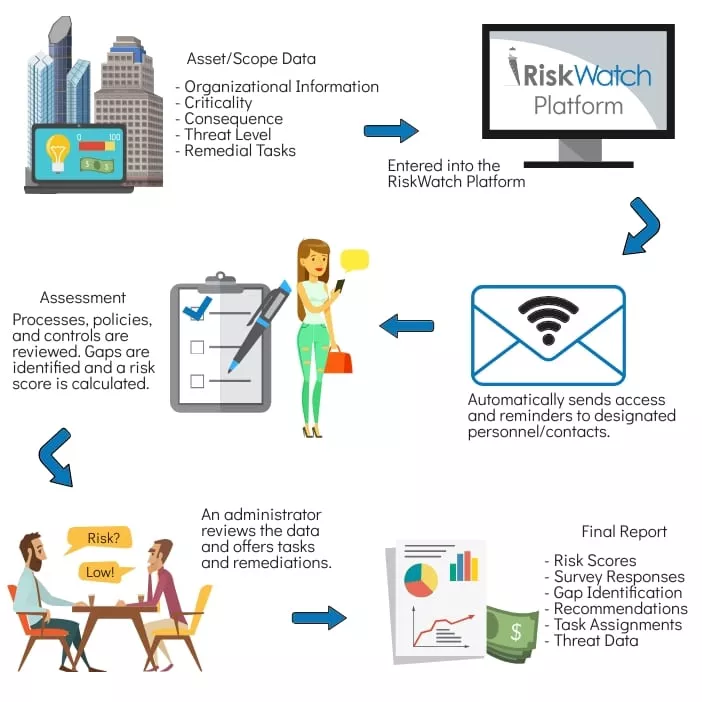
Self-Assessment Workflow
- Stage 1 - Relevant asset or scope data (Organizational information, Criticality, Consequence, Threat Level, & Evaluation Criterial) is identified and entered into the RiskWatch application.
- Stage 2 – Personnel that have the required knowledge of the organization’s processes, policies, and/or controls are identified and designated as Contacts in the application.
- Stage 3 – Surveys access is distributed by the application via email to the Contacts identified in Stage 2 to evaluate the processes, policies, and or controls in place.
- Stage 4 – Assessment is ready for analysis. Risk Scores are calculated based on Criticality, Consequence and Threat level from Stage 1 and a Gap Score based on the Survey results from Stage 3.
- Stage 5 - Gaps are identified based on the survey results. Gap mitigation recommendations are given by the application Administrator.
- Stage 6 – Remediation Tasks based on the Administrator’s recommendations (and/or recommendations provided by the Contacts) are assigned by the Administrator and managed by the application.
- Stage 7 – Final Report is Generated by the application for review by Upper Management or Auditors.
If You Need Assistance with Implementation
User Training
User Support
Custom Content
New Feature Requests
Advice and Suggestions
Your Content
Survey Content Libraries
- Adaptable to all industries
- Meet regulatory penetration testing requirements (PCI, FFIEC, HIPAA).
- Validate the effectiveness of your perimeter controls.
- DEA
- FEMA
- CIP-014
- ASIS
- C-TPAT
Performing Mobile Assessments
Upload Your Own Survey Content

Hosting
RiskWatch products are typically hosted on RiskWatch’s secure servers. They may also be hosted on your organization’s intranet infrastructure, for additional cost. For information regarding self-hosting RiskWatch products, contact RiskWatch support. If hosted in an intranet, they need access to an exchange server or an email server to send email notifications to their users.
