6 Steps to Prevent Data Breaches in 2024

6 Steps to Prevent Data Breaches in 2019 May 8, 2019 Corporate Security | Cyber Security | RiskWatch Blog | Third Party Risks How to Protect Against Data Breaches in 2024 The list of companies suffering data breaches is surprising, especially when many are sizeable companies with plenty of data security resources. Within the past […]
Risk Scoring Methodology

Risk Scoring Methodology July 31, 2019 Corporate Security | Design | Risk Assessment | Riskwatch Blog What is Risk Scoring? Risk scoring is the process of attaining a calculated score that tells you how severe a risk is, based off of several factors. Without a standard model for risk scoring, risk and security teams would […]
Service Provider Risk and Compliance

Service Provider Risk and Compliance November 7, 2018 Compliance | Corporate Security | Cyber Security | Emergency Preparedness | Managing the Risk Assessment | Regulatory Compliance | Third Party Risks Service Provider Risk and Compliance In our continuing effort to educate on the importance of risk assessment and compliance, this week we wanted to touch […]
Spear Phishing

Spear Phishing December 2, 2021 Corporate Security | Cyber Security | Riskwatch Blog What is Spear Phishing? Spear phishing is a means of electronic communication, most commonly via email, that is targeted to a specific individual or business in an attempt to steal private information from the party, such as login credentials or financial information. […]
5 Steps to Keeping Remote Meetings Safe and Secure

5 Steps to Keeping Remote Meetings Safe and Secure April 17, 2020 Corporate Security | Cyber Security | Riskwatch Blog | Third Party Risks Secure Remote Meetings Employees have finally adapted to working remotely and settled into new processes, but businesses that have enabled remote working capability shouldn’t breathe easy just yet. For many companies, […]
How to Improve the Quality of Your Company’s IT Services

How to Improve the Quality of Your Company’s IT Services April 6, 2020 Corporate Security | Cyber Security | Riskwatch Blog Information Technology is one of the fastest-growing business sectors in today’s economy. This has happened because technology has become an indispensable part of the business landscape. However, as a result, the competition in the […]
Performing a Cyber Risk Assessment
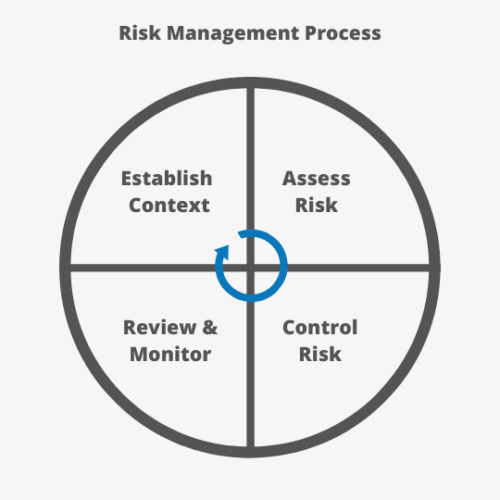
Performing a Cyber Risk Assessment March 12, 2020 Corporate Security | Cyber Security | Risk Assessment | Riskwatch Blog Performing a Cyber Risk Assessment Cyber Risk Assessments Risk assessments are crucial to any organization’s risk management strategy. A cyber risk assessment functions to identify information assets that could be impacted by a cyberattack and what […]
The Hidden Risks of a Flexible Workforce

The Hidden Risks of a Flexible Workforce February 28, 2020 Corporate Security | Cyber Security | News Room | Riskwatch Blog Changes in Workforce Flexibility The workplace has changed more in the last few years than the last two decades combined, especially in terms of flexibility. Only a fraction of the US workforce had access […]
Managing Personally Identifiable Information (PII)

Managing Personally Identifiable Information (PII) August 29, 2019 Corporate Security | Cyber Security | Identity Theft | Riskwatch Blog Managing Personally Identifiable Information In a time where discussion of cyber attacks frequents the news, customers are starting to demand more attention to their personal data – and they should. When personal information is offered or […]
Drones for Security and Risk Management

Drones for Security and Risk Management August 14, 2019 Corporate Security | Facilities Security | Risk Assessment | RiskWatch Blog Using Drones for Security and Risk Management Drones have become increasingly useful for companies looking to boost their security and risk management efforts. Their capabilities often allow security professionals to maintain a required level of […]
